Application fingerprinting hacking Bay of Plenty

Ethical Hacking Hacking Web Servers and Web Applications Sitadel is a python tool used for fingerprinting and exploiting web application vulnerabilities. The tasks are performed by fingerprinting and attack modules that come as pre-installed packages in the tool. The fingerprinting features include server, content management system (cms), frontend
Ethical Hacking Beginners to Expert Level Udemy Free
fingerprinting Darknet. 9/25/2019 · In this video from our Bypassing Web Application Firewall course your instructor, Thomas Sermpinis, will show you how to fingerprint a WAF using Burp.It's a very useful tool you've probably used before, and since fingerprinting is the first step in getting through WAF, it's a must-know., 8/11/2019 · An ethical hacker (also known as a white hat hacker) is the ultimate security professional. Ethical hackers know how to find and exploit vulnerabilities and weaknesses in various systems—just like a malicious hacker (or a black hat hacker). In fact, they both use the same skills; however, an ethical hacker uses those skills in a legitimate, lawful manner to try to find vulnerabilities and.
Here follows a complete list of Ethical Hacking and Penetration Testing Tools to be used with Kali Linux Each of the Ethical Hacking and Penetration Testing Tool contains only precise information with which you can keep yourself updated to the world of technology. Web Application Whitehat Hacking and Pentesting Teacher A.S. $650.00 $600.00 Buy this course Overview Curriculum Instructor This course (WHH201) dives you deep into the inner mechanisms of web applications and teaches you how these applications can be broken, analyzed, and …
Ethical Hacking - Beginners to Expert Level Udemy Free Download Advanced Level Penetration Testing Course,Complete Kali Linux Tutorials,Complete Cyber Security Course,Learn Kali Linux P0f is a great alternative to Nmap, a passive fingerprinting tool used to analyze network traffic and identify patterns behind TCP/IP based communications that are often blocked for Nmap active fingerprinting techniques. It includes powerful network-level fingerprinting features, as well as one that analyzes application-level payloads such as HTTP.
9 Best Application Finger Printing Tools Download. Application fingerprinting tools – The best answer to application protection and hacking What is Application fingerprinting? The answer to this question; is it is an excellent methodology to protect one’s application from any kind of security threats from hackers. 9/20/2018 · Uniscan comes with two major scanning options i-e (i) dynamic search and (ii) individual search. In dynamic search, the tool looks for all the possible vulnerabilities in the target web application. In individual search, different options can be used to achieve individual goals like web fingerprinting, server fingerprinting etc.
OS Fingerprinting in Ethical Hacking refers to any method used to determine what operating system is running on a remote computer. By analyzing certain protocol flags, options, and data in the packets a device sends onto the network, we can make relatively accurate guesses about the … Here follows a complete list of Ethical Hacking and Penetration Testing Tools to be used with Kali Linux Each of the Ethical Hacking and Penetration Testing Tool contains only precise information with which you can keep yourself updated to the world of technology.
web application fingerprinting is performed in the current scenarios, what are the visible shortcomings in the approach and then discussing about ways and means to avoid Web Application Finger Printing. Theory of Finger Printing and Web Application Finger printing Finger printing in its simplest senses is a method used to identify objects. SQL injection is one of the most common web hacking techniques. Let’s see the top 5 SQL injection tool to detect vulnerabilities! SQLMap. Sqlmap is an open source SQL injection tool that automates the process of detection and exploitation of SQL injection flaws and takes over database servers.
What is Fingerprinting? Fingerprinting, in ethical hacking, refers to any method that is used to determine the operating system that is being run on the target computer. Fingerprinting, much like Footprinting is both active and passive. Active Fingerprinting 2/16/2018 · The fingerprinting may be undertaken without any direct usage of the application, e.g. by querying a store of exposed application properties such as held in a search engine's index. Fingerprinting seeks to identity application components, whereas OAT-018 Footprinting is a more detailed analysis of how the application works. Other Names and Examples
2.1 Fingerprinting a WAF In this section, we will learn how various techniques that can be used to fingerprint some Web application firewalls. As reconnaissance is the first step towards hacking, it’s very essential to know that what we are up against before we start bypassing them. Web Application Hacking (Penetration Testing) 5-day Hands-On Course by using live hacking demonstrations and hands-on labs. The objectives of the course are to teach developers and security professionals Server & application fingerprinting Identifying the entry points File extensions handling Page enumeration and brute forcing
11/14/2017 · web-application-hacking. web-application-hacking. Trending. Vulnerability Scanning with OpenVAS 9 part 4: Custom scan configurations Uniscan Webserver fingerprinting in Kali Linux. Uniscan is a simple but great tool for Remote File Include, Local File Include and Remote Command Execution vulnerability scanner. In this tutorial we will be The DVD includes hacking tools for DNS, reconnaissance, foot-printing (gathering information about computers on the network), password cracking, network sniffing, spoofing (or masquerading) and wireless networking utilities. Here is a list of the hacking tools you can find on the Live Hacking DVD/CD: Reconnaissance (and DNS) Dig – DNS lookup
1/3/2013 · Web application fingerprinting is one of the most important aspects of the information gathering phase of ethical hacking. This allows us to narrow down the criteria instead of playing around with a large pool of possibilities. Fingerprinting simply means identification of objects using a certain You are here: Home / Latest Articles / Data Analytics & Business Intelligence / Top 25 Ethical hacking Interview Questions & Answers. Stack Fingerprinting : Once the hosts and port have been mapped by scanning the network, the final footprinting step can be performed. it is a fault created in the application code.
A WAF will be typically present in a web application where there is Strict Transport Security enabled like a banking website or an e-commerce website. While conducting a pentest, detecting the waf comes under recon, and mapping the web application architecture. One should detect the presence of a WAF & evaluate it in case of a Black Box testing. web application fingerprinting is performed in the current scenarios, what are the visible shortcomings in the approach and then discussing about ways and means to avoid Web Application Finger Printing. Theory of Finger Printing and Web Application Finger printing Finger printing in its simplest senses is a method used to identify objects.
2/16/2018 · The fingerprinting may be undertaken without any direct usage of the application, e.g. by querying a store of exposed application properties such as held in a search engine's index. Fingerprinting seeks to identity application components, whereas OAT-018 Footprinting is a more detailed analysis of how the application works. Other Names and Examples 7/16/2018 · Webpwn3r can detect WAF (Web Application Firewall) technologies such as Web Knight , it also performs XSS vulnerability scanning on the target web applications. The other features include the fingerprinting of the backend technologies of the target web applications and scanning for SQL injection vulnerabilities on the target web application.
Cybersecurity Fingerprinting What is it? Fingerprint

OAT-004 Fingerprinting OWASP. 7/16/2018 · Webpwn3r can detect WAF (Web Application Firewall) technologies such as Web Knight , it also performs XSS vulnerability scanning on the target web applications. The other features include the fingerprinting of the backend technologies of the target web applications and scanning for SQL injection vulnerabilities on the target web application., 9/20/2018 · Uniscan comes with two major scanning options i-e (i) dynamic search and (ii) individual search. In dynamic search, the tool looks for all the possible vulnerabilities in the target web application. In individual search, different options can be used to achieve individual goals like web fingerprinting, server fingerprinting etc..
10 Best WiFi Password Hacker Apps for Android without Root. 7/16/2018 · Webpwn3r can detect WAF (Web Application Firewall) technologies such as Web Knight , it also performs XSS vulnerability scanning on the target web applications. The other features include the fingerprinting of the backend technologies of the target web applications and scanning for SQL injection vulnerabilities on the target web application., You are here: Home / Latest Articles / Data Analytics & Business Intelligence / Top 25 Ethical hacking Interview Questions & Answers. Stack Fingerprinting : Once the hosts and port have been mapped by scanning the network, the final footprinting step can be performed. it is a fault created in the application code..
Fingerprinting Identifying Applications
Web App Hacking Part 15 Web site Fingerprinting with Whatweb. What is Ethical Hacking Fingerprinting? Fingerprinting in Ethical Hacking means a method used for determining the current running operating system on a remote computer. Fingerprinting can be … https://en.wikipedia.org/wiki/Fingerprint_(computing) 11/14/2017 · web-application-hacking. web-application-hacking. Trending. Vulnerability Scanning with OpenVAS 9 part 4: Custom scan configurations Uniscan Webserver fingerprinting in Kali Linux. Uniscan is a simple but great tool for Remote File Include, Local File Include and Remote Command Execution vulnerability scanner. In this tutorial we will be.
11/1/2011 · Application security expert Michael Cobb explains how targeting application fingerprinting can be security's first line of defense. This is commonly known as Google hacking. By using Google's Sitadel is a python tool used for fingerprinting and exploiting web application vulnerabilities. The tasks are performed by fingerprinting and attack modules that come as pre-installed packages in the tool. The fingerprinting features include server, content management system (cms), frontend
11/1/2011 · Application security expert Michael Cobb explains how targeting application fingerprinting can be security's first line of defense. This is commonly known as Google hacking. By using Google's OS Fingerprinting in Ethical Hacking refers to any method used to determine what operating system is running on a remote computer. By analyzing certain protocol flags, options, and data in the packets a device sends onto the network, we can make relatively accurate guesses about the …
Understanding web testing - [Narrator] Fingerprinting is an important first step in testing a web application. As the environment in which it operates, is as important as the application itself This category is home to all Security Specialists and Ethical Hackers. Cyber Security and Ethical hacking is a practice to improve the Security of network and applications to prevent unauthorized access.
1/3/2013 · Web application fingerprinting is one of the most important aspects of the information gathering phase of ethical hacking. This allows us to narrow down the criteria instead of playing around with a large pool of possibilities. Fingerprinting simply means identification of objects using a certain OS Fingerprinting in Ethical Hacking refers to any method used to determine what operating system is running on a remote computer. By analyzing certain protocol flags, options, and data in the packets a device sends onto the network, we can make relatively accurate guesses about the …
Here follows a complete list of Ethical Hacking and Penetration Testing Tools to be used with Kali Linux Each of the Ethical Hacking and Penetration Testing Tool contains only precise information with which you can keep yourself updated to the world of technology. 1/1/2005 · Hacker techniques and exploits: Prevent system fingerprinting, probing during Web application fingerprinting Hackers use Web application fingerprinting to learn about their target. You can
Google hacking refers to collecting information using google dorks (keywords) by constructing search queries which result in finding sensitive information.details collected include compromised passwords, default credentials, competitor information, information related to a particular topic etc P0f is a great alternative to Nmap, a passive fingerprinting tool used to analyze network traffic and identify patterns behind TCP/IP based communications that are often blocked for Nmap active fingerprinting techniques. It includes powerful network-level fingerprinting features, as well as one that analyzes application-level payloads such as HTTP.
This category is home to all Security Specialists and Ethical Hackers. Cyber Security and Ethical hacking is a practice to improve the Security of network and applications to prevent unauthorized access. What is Ethical Hacking Fingerprinting? Fingerprinting in Ethical Hacking means a method used for determining the current running operating system on a remote computer. Fingerprinting can be …
9/25/2019 · In this video from our Bypassing Web Application Firewall course your instructor, Thomas Sermpinis, will show you how to fingerprint a WAF using Burp.It's a very useful tool you've probably used before, and since fingerprinting is the first step in getting through WAF, it's a must-know. What is Fingerprinting? Fingerprinting, in ethical hacking, refers to any method that is used to determine the operating system that is being run on the target computer. Fingerprinting, much like Footprinting is both active and passive. Active Fingerprinting
Nmap is of course of the most famous port scanners and hacking tools of all time, the last stable release was back in July 2009. For those that may not know, Nmap (“Network Mapper”) is a free open source utility for network exploration or security auditing. 11/14/2017 · web-application-hacking. web-application-hacking. Trending. Vulnerability Scanning with OpenVAS 9 part 4: Custom scan configurations Uniscan Webserver fingerprinting in Kali Linux. Uniscan is a simple but great tool for Remote File Include, Local File Include and Remote Command Execution vulnerability scanner. In this tutorial we will be
Ethical Hacking - Tools - In this chapter, we will discuss in brief some of famous tools that are widely used to prevent hacking and getting unauthorized access to a computer or network BlindElephant is an open-source generic web application fingerprinter that produces results by comparing a small set of static files at known locations against precomputed hashes for versions of those files in all available releases. The technique is fast, low-bandwidth, non-invasive, generic, and highly automatable.
Here follows a complete list of Ethical Hacking and Penetration Testing Tools to be used with Kali Linux Each of the Ethical Hacking and Penetration Testing Tool contains only precise information with which you can keep yourself updated to the world of technology. 7/16/2018 · Webpwn3r can detect WAF (Web Application Firewall) technologies such as Web Knight , it also performs XSS vulnerability scanning on the target web applications. The other features include the fingerprinting of the backend technologies of the target web applications and scanning for SQL injection vulnerabilities on the target web application.
A prototype model for web application fingerprinting w3
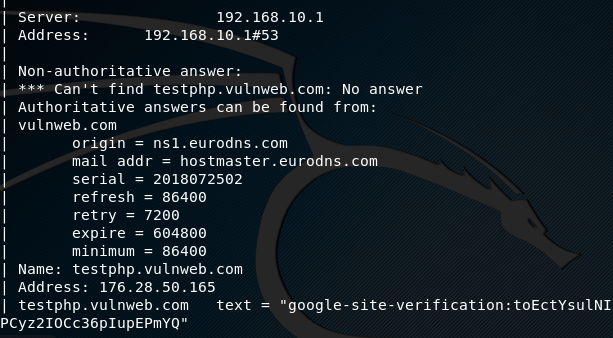
Fingerprinting web servers LinkedIn Learning formerly. OS Fingerprinting in Ethical Hacking refers to any method used to determine what operating system is running on a remote computer. By analyzing certain protocol flags, options, and data in the packets a device sends onto the network, we can make relatively accurate guesses about the …, Ethical Hacking - Overview. Hacking has been a part of computing for almost five decades and it is a very broad discipline, which covers a wide range of topics. The first known event of hacking had taken place in 1960 at MIT and at the same time, the term "Hacker" was originated..
Cyber Security & Ethical Hacking Questions Edureka Community
Fingerprinting WAF with Burp [ FREE COURSE CONTENT]. 8/10/2015 · Uniscan is a simple but great tool for Remote File Include, Local File Include and Remote Command Execution vulnerability scanner. In this tutorial we will be exploring the webserver fingerprinting functionality in Uniscan on Kali Linux., 7/16/2018 · Webpwn3r can detect WAF (Web Application Firewall) technologies such as Web Knight , it also performs XSS vulnerability scanning on the target web applications. The other features include the fingerprinting of the backend technologies of the target web applications and scanning for SQL injection vulnerabilities on the target web application..
It has many other advanced features like OS fingerprinting, SYN scan and others, and it’s an open source application, meaning that you will never get out of date. Related: Top 5 Best Games Hacking Apps For Android with/without Root. Conclusion This category is home to all Security Specialists and Ethical Hackers. Cyber Security and Ethical hacking is a practice to improve the Security of network and applications to prevent unauthorized access.
Understanding web testing - [Narrator] Fingerprinting is an important first step in testing a web application. As the environment in which it operates, is as important as the application itself Web App Hacking, Part 15: Web site Fingerprinting with Whatweb . Welcome back, my aspiring cyber warriors! (Web Application Firewall) that blocks these scans. Without using the stealthy switch, the WAF will block our scan and tell us that the site doesn't use WordPress.
11/1/2011 · Application security expert Michael Cobb explains how targeting application fingerprinting can be security's first line of defense. This is commonly known as Google hacking. By using Google's Nmap is of course of the most famous port scanners and hacking tools of all time, the last stable release was back in July 2009. For those that may not know, Nmap (“Network Mapper”) is a free open source utility for network exploration or security auditing.
1/3/2013 · Web application fingerprinting is one of the most important aspects of the information gathering phase of ethical hacking. This allows us to narrow down the criteria instead of playing around with a large pool of possibilities. Fingerprinting simply means identification of objects using a certain 9/25/2019 · In this video from our Bypassing Web Application Firewall course your instructor, Thomas Sermpinis, will show you how to fingerprint a WAF using Burp.It's a very useful tool you've probably used before, and since fingerprinting is the first step in getting through WAF, it's a must-know.
Web App Hacking, Part 15: Web site Fingerprinting with Whatweb . Welcome back, my aspiring cyber warriors! (Web Application Firewall) that blocks these scans. Without using the stealthy switch, the WAF will block our scan and tell us that the site doesn't use WordPress. P0f is a great alternative to Nmap, a passive fingerprinting tool used to analyze network traffic and identify patterns behind TCP/IP based communications that are often blocked for Nmap active fingerprinting techniques. It includes powerful network-level fingerprinting features, as well as one that analyzes application-level payloads such as HTTP.
6/6/2019 · Java Project Tutorial - Make Login and Register Form Step by Step Using NetBeans And MySQL Database - Duration: 3:43:32. 1BestCsharp blog 4,586,199 views 2/16/2018 · The fingerprinting may be undertaken without any direct usage of the application, e.g. by querying a store of exposed application properties such as held in a search engine's index. Fingerprinting seeks to identity application components, whereas OAT-018 Footprinting is a more detailed analysis of how the application works. Other Names and Examples
Sitadel is a python tool used for fingerprinting and exploiting web application vulnerabilities. The tasks are performed by fingerprinting and attack modules that come as pre-installed packages in the tool. The fingerprinting features include server, content management system (cms), frontend SQL injection is one of the most common web hacking techniques. Let’s see the top 5 SQL injection tool to detect vulnerabilities! SQLMap. Sqlmap is an open source SQL injection tool that automates the process of detection and exploitation of SQL injection flaws and takes over database servers.
BlindElephant is an open-source generic web application fingerprinter that produces results by comparing a small set of static files at known locations against precomputed hashes for versions of those files in all available releases. The technique is fast, low-bandwidth, non-invasive, generic, and highly automatable. BlindElephant is an open-source generic web application fingerprinter that produces results by comparing a small set of static files at known locations against precomputed hashes for versions of those files in all available releases. The technique is fast, low-bandwidth, non-invasive, generic, and highly automatable.
642.5 HANDS ON: Web Application Firewall and Filter Bypass Applications today are using more security controls to help prevent attacks. These controls, such as Web Application Firewalls and filtering techniques, make it more difficult for penetration testers during their testing. The controls block many of the automated tools and simple techniques 8/10/2015 · Uniscan is a simple but great tool for Remote File Include, Local File Include and Remote Command Execution vulnerability scanner. In this tutorial we will be exploring the webserver fingerprinting functionality in Uniscan on Kali Linux.
FOCA (Fingerprinting Organizations with Collected Archives) is a tool used mainly to find metadata and hidden information in the documents its scans. These documents may be on web pages, and can be downloaded and analyzed with FOCA. It is capable of analyzing a wide variety of documents, with the most common being Microsoft Office, Open Office, or PDF files, although it also analyzes Adobe 6/6/2019 · Java Project Tutorial - Make Login and Register Form Step by Step Using NetBeans And MySQL Database - Duration: 3:43:32. 1BestCsharp blog 4,586,199 views
What is Ethical Hacking Fingerprinting? Fingerprinting in Ethical Hacking means a method used for determining the current running operating system on a remote computer. Fingerprinting can be … 8/10/2015 · Uniscan is a simple but great tool for Remote File Include, Local File Include and Remote Command Execution vulnerability scanner. In this tutorial we will be exploring the webserver fingerprinting functionality in Uniscan on Kali Linux.
Hacker techniques and exploits Prevent system
W3-Scrape A Windows based Reconnaissance Tool for Web. web application fingerprinting is performed in the current scenarios, what are the visible shortcomings in the approach and then discussing about ways and means to avoid Web Application Finger Printing. Theory of Finger Printing and Web Application Finger printing Finger printing in its simplest senses is a method used to identify objects., web application fingerprinting is performed in the current scenarios, what are the visible shortcomings in the approach and then discussing about ways and means to avoid Web Application Finger Printing. Theory of Finger Printing and Web Application Finger printing Finger printing in its simplest senses is a method used to identify objects..
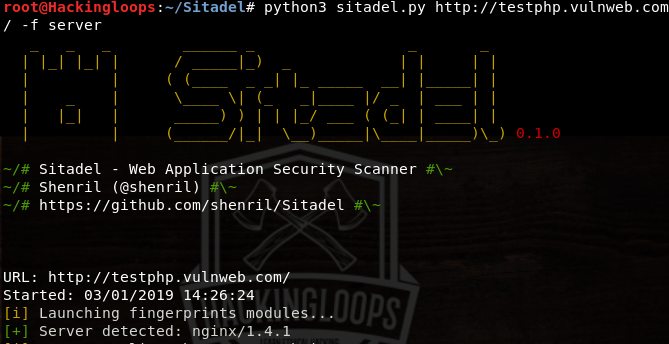
Ethical Hacking Fingerprinting in Ethical Hacking Tutorial. Sitadel is a python tool used for fingerprinting and exploiting web application vulnerabilities. The tasks are performed by fingerprinting and attack modules that come as pre-installed packages in the tool. The fingerprinting features include server, content management system (cms), frontend, OS Fingerprinting in Ethical Hacking refers to any method used to determine what operating system is running on a remote computer. By analyzing certain protocol flags, options, and data in the packets a device sends onto the network, we can make relatively accurate guesses about the ….
What is OS Fingerprinting and Techniques Zerosuniverse
Webpwn3r – Web Application Vulnerability Scanner Latest. 9/22/2005 · Find a hacker by fingerprinting the bad guys. Stop hackers from finding data during Web application fingerprinting Hackers use Web application fingerprinting to learn about their target. You https://en.wikipedia.org/wiki/Fingerprint_(computing) 9 Best Application Finger Printing Tools Download. Application fingerprinting tools – The best answer to application protection and hacking What is Application fingerprinting? The answer to this question; is it is an excellent methodology to protect one’s application from any kind of security threats from hackers..
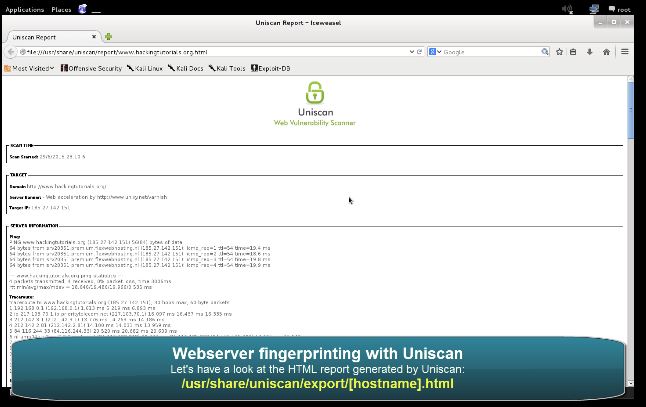
A WAF will be typically present in a web application where there is Strict Transport Security enabled like a banking website or an e-commerce website. While conducting a pentest, detecting the waf comes under recon, and mapping the web application architecture. One should detect the presence of a WAF & evaluate it in case of a Black Box testing. 9/20/2018 · Uniscan comes with two major scanning options i-e (i) dynamic search and (ii) individual search. In dynamic search, the tool looks for all the possible vulnerabilities in the target web application. In individual search, different options can be used to achieve individual goals like web fingerprinting, server fingerprinting etc.
In this course, find out how to test your sites and applications for weaknesses. Cybersecurity expert Malcolm Shore examines the various parts of a web application and introduces the Open Web Application Security Project (OWASP), which provides documentation, tools, … Here follows a complete list of Ethical Hacking and Penetration Testing Tools to be used with Kali Linux Each of the Ethical Hacking and Penetration Testing Tool contains only precise information with which you can keep yourself updated to the world of technology.
9/22/2005 · Find a hacker by fingerprinting the bad guys. Stop hackers from finding data during Web application fingerprinting Hackers use Web application fingerprinting to learn about their target. You Ethical Hacking - Overview. Hacking has been a part of computing for almost five decades and it is a very broad discipline, which covers a wide range of topics. The first known event of hacking had taken place in 1960 at MIT and at the same time, the term "Hacker" was originated.
BlindElephant is an open-source generic web application fingerprinter that produces results by comparing a small set of static files at known locations against precomputed hashes for versions of those files in all available releases. The technique is fast, low-bandwidth, non-invasive, generic, and highly automatable. Ethical Hacking - Beginners to Expert Level Udemy Free Download Advanced Level Penetration Testing Course,Complete Kali Linux Tutorials,Complete Cyber Security Course,Learn Kali Linux
Ethical Hacking - Overview. Hacking has been a part of computing for almost five decades and it is a very broad discipline, which covers a wide range of topics. The first known event of hacking had taken place in 1960 at MIT and at the same time, the term "Hacker" was originated. 1/3/2013 · Web application fingerprinting is one of the most important aspects of the information gathering phase of ethical hacking. This allows us to narrow down the criteria instead of playing around with a large pool of possibilities. Fingerprinting simply means identification of objects using a certain
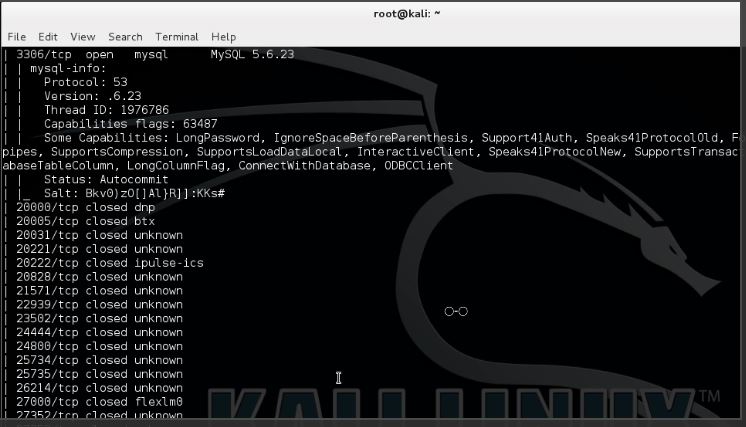
Web Server fingerprinting is Critical . If you know the version and the type of the web server during penetration Testing , it will allow you to easily determine the type of vulnerabilities already been discovered in that Type and Version of Web server , also will help you to determine the 2/16/2018 · The fingerprinting may be undertaken without any direct usage of the application, e.g. by querying a store of exposed application properties such as held in a search engine's index. Fingerprinting seeks to identity application components, whereas OAT-018 Footprinting is a more detailed analysis of how the application works. Other Names and Examples
SQL injection is one of the most common web hacking techniques. Let’s see the top 5 SQL injection tool to detect vulnerabilities! SQLMap. Sqlmap is an open source SQL injection tool that automates the process of detection and exploitation of SQL injection flaws and takes over database servers. 642.5 HANDS ON: Web Application Firewall and Filter Bypass Applications today are using more security controls to help prevent attacks. These controls, such as Web Application Firewalls and filtering techniques, make it more difficult for penetration testers during their testing. The controls block many of the automated tools and simple techniques
5/14/2019 · Web App Hacking, Part 15: Web site Fingerprinting with Whatweb. (see Web Technologies here). In most cases, before we develop a hacking strategy of the web site, we need to understand the technologies employed in building the website. Web site attacks are not generic. use Apache as their web server and an Incapsula Web Application 5/14/2019 · Web App Hacking, Part 15: Web site Fingerprinting with Whatweb. (see Web Technologies here). In most cases, before we develop a hacking strategy of the web site, we need to understand the technologies employed in building the website. Web site attacks are not generic. use Apache as their web server and an Incapsula Web Application
A WAF will be typically present in a web application where there is Strict Transport Security enabled like a banking website or an e-commerce website. While conducting a pentest, detecting the waf comes under recon, and mapping the web application architecture. One should detect the presence of a WAF & evaluate it in case of a Black Box testing. OS Fingerprinting in Ethical Hacking refers to any method used to determine what operating system is running on a remote computer. By analyzing certain protocol flags, options, and data in the packets a device sends onto the network, we can make relatively accurate guesses about the …
What is Ethical Hacking Fingerprinting? Fingerprinting in Ethical Hacking means a method used for determining the current running operating system on a remote computer. Fingerprinting can be … 642.5 HANDS ON: Web Application Firewall and Filter Bypass Applications today are using more security controls to help prevent attacks. These controls, such as Web Application Firewalls and filtering techniques, make it more difficult for penetration testers during their testing. The controls block many of the automated tools and simple techniques
9/25/2019 · In this video from our Bypassing Web Application Firewall course your instructor, Thomas Sermpinis, will show you how to fingerprint a WAF using Burp.It's a very useful tool you've probably used before, and since fingerprinting is the first step in getting through WAF, it's a must-know. Here follows a complete list of Ethical Hacking and Penetration Testing Tools to be used with Kali Linux Each of the Ethical Hacking and Penetration Testing Tool contains only precise information with which you can keep yourself updated to the world of technology.